Pentesting in 2026: Black, White, or Gray Box?
In the current corporate environment, cybersecurity investment must be precise and strategic. A common error among executives is requesting an intrusion test without defining the appropriate scope or modality, resulting in a false sense of security or inefficient resource allocation. Understanding pentesting types differences is fundamental to aligning technical evaluation with business objectives.
The uncertainty regarding whether your systems would withstand a real attack today is the primary client pain point. Choosing the incorrect modality can leave critical vectors unaudited. Do you need to simulate a blind external attack or verify the internal security of a critical application? The answer defines the difference between merely meeting a requirement and truly ensuring operational continuity.
Aligning Offensive Strategy with Security Maturity
There is no one-size-fits-all approach to assurance. The choice between the different modalities depends on the organization’s cybersecurity maturity level and the specific threat being mitigated. While a comprehensive audit seeks to eliminate every configuration error, a real attack simulation prioritizes the exploitation routes a cybercriminal would use to cause immediate damage.
Hacking Mode addresses this challenge through initial consulting that determines the relevant “attack surface”. The goal is to transform uncertainty into actionable data, allowing the organization to anticipate security breaches before they become public incidents.+1
Technical Modalities and Use Cases
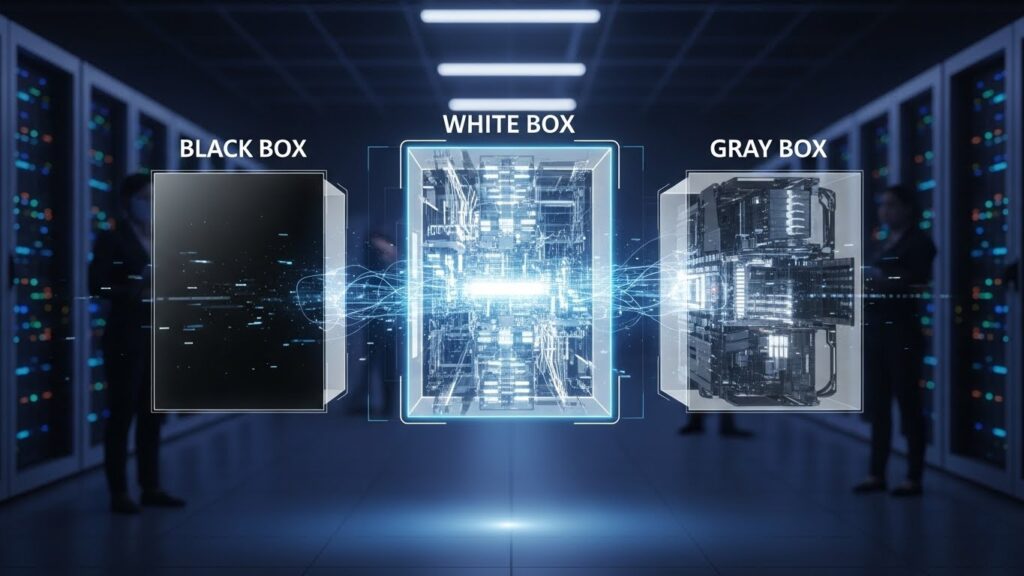
Below, we break down the three industry-standard methodologies to clarify their strategic application:
- Black Box Pentesting: The most realistic simulation of an external cyberattack. Hacking Mode consultants operate without prior knowledge of the infrastructure, replicating the view of a hacker seeking to breach the perimeter from the internet. It is ideal for validating the resistance of the first line of defense.
- White Box Pentesting: Also known as “Crystal Box,” this implies full access to documentation, source code, and network diagrams. This modality allows for a comprehensive and deep audit, ideal for development phases or critical systems where not a single hidden vulnerability can be tolerated.
- Gray Box Pentesting: The strategic balance. The offensive team possesses partial access, such as standard user credentials. This simulates insider threats or a scenario where an employee account has been compromised, evaluating lateral movement and privilege escalation within the network.
- Authority Standards: All our executions align with international frameworks like PTES (Penetration Testing Execution Standard) and OSSTMM to ensure auditable, high-quality results.
Conclusion
Offensive security is not just about finding flaws; it is about validating your company’s Operational Resilience against adverse scenarios. Understanding technical differences allows you to make informed decisions that maximize the return on security investment. Hacking Mode positions itself as your Strategic Partner, guiding you not only in test execution but in the continuous strengthening of your security posture. By selecting the correct modality, you transform a technical requirement into a trusted competitive advantage.
👉 Test your security before hackers do. Schedule your Pentest.
🌎 GLOBAL ATTENTION & COVERAGE
📞 Phone / WhatsApp:
- 🇲🇽 MX: +52 1 55 5550 5537
- 🇺🇸 USA: +1 (918) 540-9341
📧 Email Support & Sales:
🌐 Global Coverage & Service Locations We provide immediate attention, strategic consulting, and deployment of Security Compliance Specialists and Cybersecurity Experts across the entire Americas, ensuring business continuity in the main markets of:
- 🇺🇸 United States: Miami, Houston, New York, San Francisco, Los Angeles, among others.
- 🇲🇽 Mexico: Mexico City (CDMX), Monterrey, Guadalajara, Queretaro, Tijuana (Nationwide Coverage).
- 🇬🇹 Guatemala: Guatemala City, Quetzaltenango, Escuintla, Antigua Guatemala (Nationwide Coverage).
- 🌎 Latin America: Bogota, Medellin, Lima, Santiago de Chile, Buenos Aires, Sao Paulo, Panama City, serving the entire region.
Tags: #HackingMode #Cybersecurity #SecurityCompliance #HackingRED #Pentesting2026